Signing an executable hello.exe:
Note that you need to have and install a valid code-signing certificate. The current certificate I am using here is a cert signed by Sectigo. I will try to return to this to add instructions for doing this.
Assuming you have your cert installed and signtool.exe on your path, this below will sign a file that will be considered valid as long as your certificate is valid and the current date is within the time covered by your certificate.
signtool sign hello.exe
Doing the following additionally to the signed file above will link it to a current time stamp. As long as your certificate is valid at the time of signing and it remains valid, the signed file will be valid.
signtool timestamp /t http://timestamp.sectigo.com hello.exe
---
Below is a cut and paste from an entry I made on Stackoverflow. I originally was asking how to do something but I was able to answer it myself before I got an answer:
How can I sign an Oracle VirtualBox virtual appliance (.OVA)
I want to sign an Oracle VirtualBox Virtual Appliance, an OVA file. I am looking for instructions.
I have had extensive conversations with Comodo and Sectigo. They don't know how and had trouble even understanding the question.
When I load my VM in VirtualBox it says that it is unsigned but gives no information as to how to correct that. I have a code signing certificate, and I have no trouble signing and timestamping an executable file:
signtool sign /t http://timestamp.comodoca.com t_hello.exe Done Adding Additional Store Successfully signed: t_hello.exe
Attempting with an .ova file gives an error:
signtool sign /t http://timestamp.comodoca.com ACoreTpl.ova Done Adding Additional Store SignTool Error: This file format cannot be signed because it is not recognized. SignTool Error: An error occurred while attempting to sign: ACoreTpl.ova
I took a shot at downloading a tool from VMWare, but it did not work on my VirtualBox appliance. It just gave error messages.
Unless the error message is meaningless and just hardcoded in VirtualBox, there is code inspecting something. I really don't want to go fishing through the code, but at this point it seems like I might have to.
The purpose of this exercise is so that I can publish a working system as a virtual appliance that is 'known good' and can be verified as the real thing when it loads.
Answer from Myself:
[Note: There are images in the document I pasted this from, but they would not paste in here.] I was able to muddle through a work-around. The workaround involves getting a tool from VMWare (ovftool.exe), which seems a bit strange. It allows the import of the OVA, showing the certificate and marking it as 'safe'. It still has a couple of issues. One is an annoying warning message issued while creating the signed file, for which I was unable to find a cure. The other is that it does not seem to contact a timeserver to timestamp the file. Presumably that means that when the signing certificate expires, you get warnings again when loading.
I would still like to know how you are supposed to do it properly according to Oracle. Surely, Oracle is not using VMWare's software to sign their Virtual Appliances.
This is my journey under Windows 10. At the end, I have a publishable appliance.
You need a virtual appliance (*.ova)
You need a signing certificate.
You need to have OpenSSL installed.
You need the program ovftool.exe from VMWare
To get the .ova file, you need to export one of your VMs as a virtual appliance:
Open the export virtual appliance dialog:
File->Export Appliance [Alternatively E]
Choose the virtual machine to export. Fill in whatever Virtual system settings apply.
For appliance settings, set the Format to Open Virtualization Format 1.0
Make sure the 'Write Manifest file' checkbox is checked.
Click on the button to write file.
You should have the signing certificate installed in the certificate store. If you don't have this already, you need to consult your certificate provider.
To get the signing certificate in a usable form, you have to jump through a few hoops to get an old-timey Privacy Enhanced Mail (PEM) file.
You need to get the certificate into a file first.
Start the Certificate Manager by running certmgr.msc
Open Personal->Certificates and right-click on your signing certificate
Open the All tasks menu and choose Export
This should open the Certificate Export Wizard
Click [Next]
Choose the radio button marked "Yes, export the private key"
Click [Next]
Choose "Personal Information Exchange - PKCS (.PFX)"
Check "Include all certificates in the certification path if possible"
Check "Export all extended properties"
Check "Enable certificate privacy"
Click [Next]
Check the Password checkbox, and enter and confirm a password [using password "IMPPass" in this example]
Change the Encryption dropdown to AES256-SHA256
Click [Next]
Assign the filename and path for the exported certificate. In this example, I called it "MyCert". Note that you don't put the file extension on the name here. The Certificate Export Wizard adds it when it writes the file. You should save it on the path where you saved the OVA file.
Click [Next]
Review settings and Click
It should pop up a message box saying the export was successful. Dismiss it by clicking on the button.
You need to do the next steps at the command line.
Open a console window.
Change to the directory where you have saved your OVA and PFX files.
cd c:<yoursavelocation>
You now need to convert the certificate to a form that can be used (.pem). To do this, you need to use OpenSSL. Here is the form of the command:
openssl pkcs12 -in MyCert.pfx -out MyCert.pem
Respond to the prompts for Import Password and PEM pass phrase:
Enter Import Password: IMPPass
Enter PEM pass phrase: PEMPass
Verifying - Enter PEM pass phrase: PEMPass
Finally, you can sign the exported OVA with ovftool with a command like this:
ovftool --privateKey=MyCert.pem --shaAlgorithm=SHA1 DamnSmall.ova DSL.ova
Opening OVA source: DamnSmall.ova
Opening OVA target: DSL.ova
Writing OVA package: DSL.ova
Transfer Completed
The manifest validates
Enter passphrase for MyCert.pem: PEMPass
A warning is issued here, but it will not interfere with the signing.
Warning:
No supported manifest(sha1, sha256, sha512) entry found for: 'DamnSmall-disk001.vmdk'. Completed successfully
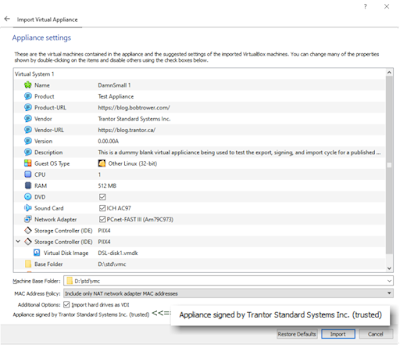
At this point, there should be a signed file called DSL.ova. It will indicate that when imported in VirtualBox.
To test, import the newly created and signed OVA file. Open the import dialog:
File->Import Appliance or alternatively I
Enter the path and name of the signed Virtual Appliance. Click [Next]
The Appliance settings dialog should have text in the bottom left corner indicating that you have signed the appliance, and that it is trusted.
Appliance is signed


No comments:
Post a Comment